Two-Step Verification
Although data security is our top priority and we do everything that is reasonably possible to keep your account and data safe, there are many factors beyond our control that may compromise the security of your account, and thereby your lab's research data (e.g. key loggers on public computers, reuse of password for other applications that have been exposed, etc.). Therefore, we recommend using two-step verification - also known as two-factor authentication - to improve the security of your account. When activated, two-step verification will require you to provide a secret code upon login, in addition to your username and password. Check out the video below to see how two-step verification works:
Activate two-step verification under the Two-Step Verification tab with the Account Settings page.
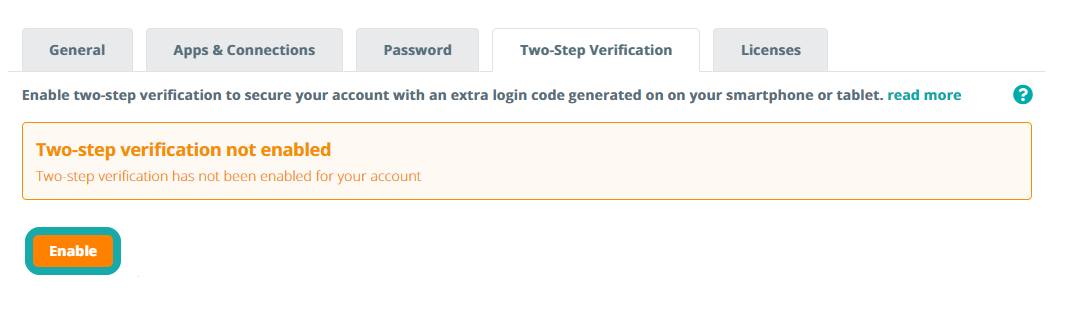
Enabling two-step verification for your account introduces a second layer of security to protect your account. With two-step verification active, an additional 6-digit code is required in order to log into the application. This unique code is generated on your smartphone and changes every 60 seconds. First, you need to activate the two-step verification setting by clicking Enable.
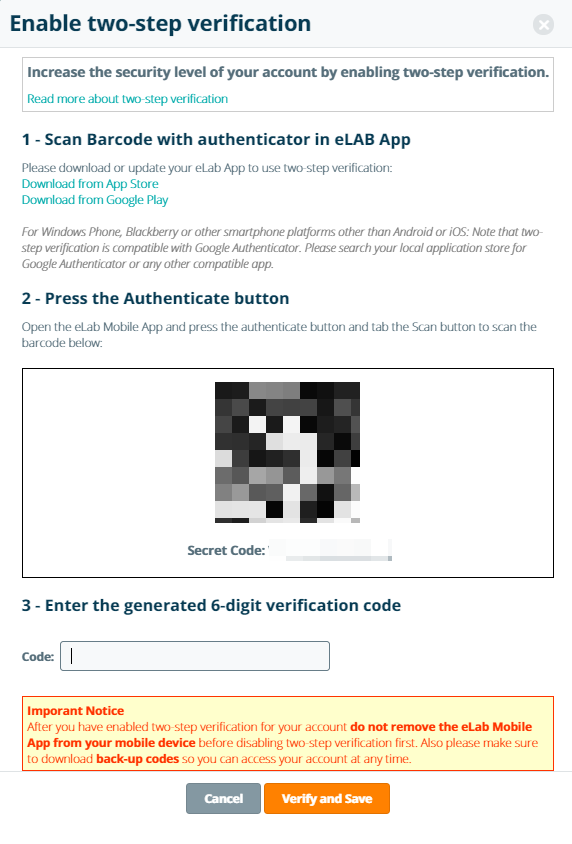
In the pop-up menu, you can now verify your device to generate a two-factor code. You can get this code by following the instructions below. Please note that after enabling two-step verification, you will always need your mobile device to generate a new two-factor code when logging into eLabProtocols. If you do not have this code, you may no longer be able to directly access your account and data.
There are several options for generating two-step verification codes:
- The eLabJournal or eLabInventory Mobile App – Download and install the App of iOS or Android
- Google Authenticator Mobile App – If you already use Google Authenticator for other applications (for Windows Phone use Microsoft Authenticator)
- WinAuth Desktop App – if you do not have a smartphone, you can download and install WinAuth on your desktop
- Protectimus SLIM mini – physical card that can be programmed using NFC to generate 2FA tokens. Read more about Protectimus SLIM mini
Install the application of your choice and either scan the barcode displayed when enabling two-step verification, or manually enter the secret key listed below the barcode. After scanning or entering the secret code, the application will begin generating a time-based unique 6-digit code (the two-factor code) that changes every 60 seconds. This is the code you need to finish activating the two-step verification and to login moving forward.
- Enter the 6-digit code
- Click Verify and Save
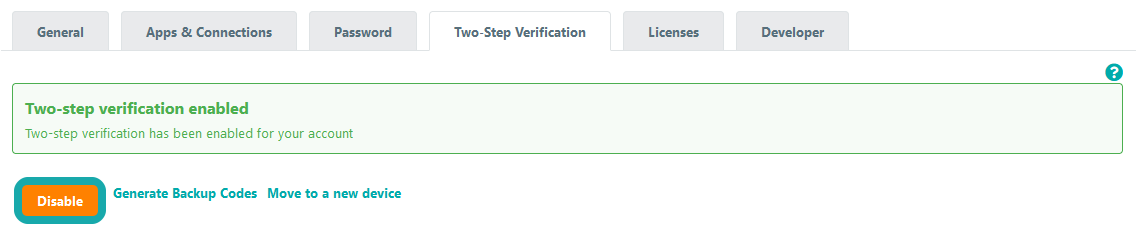
Two-step verification is now enabled. Please make sure to never remove the app from your authenticated device before disabling the two-step verification setting first. We also recommend that you download the back-up two-factor codes, which can each be used once to access the application if you lose your two-factor code generation device. In the event that your account is blocked while two-step verification is enabled, this setting can be disabled by an administrator via the Organization Admin Panel. Cloud users can alternatively contact our Support Desk to disable two-step verification on their account.
When two-step verification is active, you need to enter the two-step verification code every time your login. There is an option to trust the computer for 30 days, which means that you only have to enter the two-step verification code once every 30 days. This option is linked to a specific IP address and computer to ensure that your account remains protected with two-factor authentication when logging in from a different device.
As a group administrator, you can enforce two-step verification for all members in the lab by changing the Group Policy. Navigate to My Groups and click Edit. In the Group Policy tab, you can enable the option to make two-step verification mandatory for all lab members.
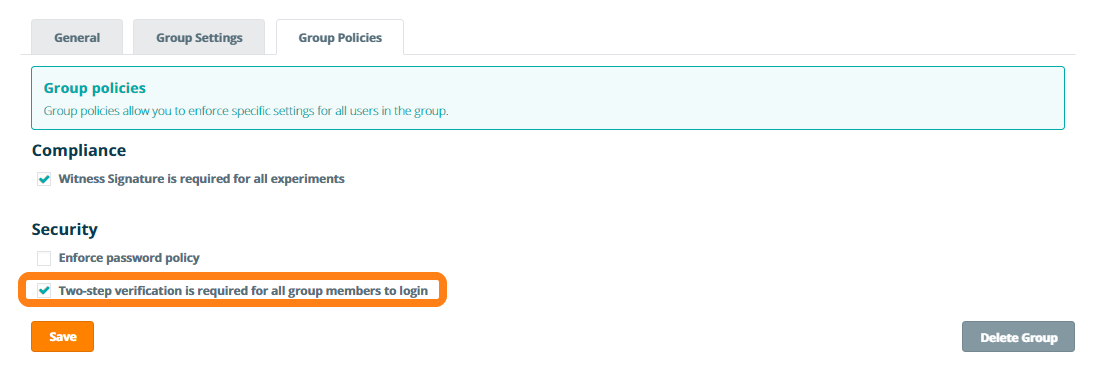
When enabling this option, all users in the lab will be forced to activate two-step verification for their account during their next login. The user will only be allowed to access their account once they have successfully setting up two-step verification.